Patching your AWS EC2 instance for the Meltdown/Spectre vulnerabilities
Intro
The patches we will be applying bring the KPTI (kernel page-table isolation), a Linux kernel feature that mitigates the Meltdown security vulnerability. The title of this post is therefore a misnomer - there are no Spectre patches yet, but by convention all three known variants of these vulnerabilities are jointly referred to as Meltdown/Spectre. I will update this post when this changes.
Updating the instance with the patched kernel
I will describe the steps based on AWS instance running Ubuntu 14.04.5 LTS and GNU/Linux 4.4.0-97-generic kernel prior to applying the patch.
The most up-to-date information on Spectre and Meltdown for Ubuntu can be found here: https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown It also contains recommended kernel images for various distro versions.
Step 1) SSH into your instance:
ssh ubuntu@instance.region.compute.amazonaws.com
Update the repositories:
sudo apt-get update
As of writing this post Canonical recommends kernel image 3.13.0-139.188 for Ubuntu 14.04 using 3.13 and 4.4.0-109.132 if you are using the xenial kernel backport (4.4.0), so let’s install those:
sudo apt-get install linux-headers-4.4.0-109 linux-headers-4.4.0-109-generic linux-image-4.4.0-109-generic linux-image-extra-4.4.0-109-generic --fix-missing
Step 2) reboot you instance
You can quickly reboot an instance using the command line if you have configured AWS CLI:
aws ec2 reboot-instances --instance-ids instance-id --region region
or with the EC2 console.
- Open the Amazon EC2 console.
- In the navigation pane, choose Instances.
- Select the instance and choose Actions, Instance State, Reboot.
- Choose Yes, Reboot when prompted for confirmation.
Step 3) so did it work?
Check if the instance is back online:
aws ec2 describe-instance-status --instance-id instance-id --region region
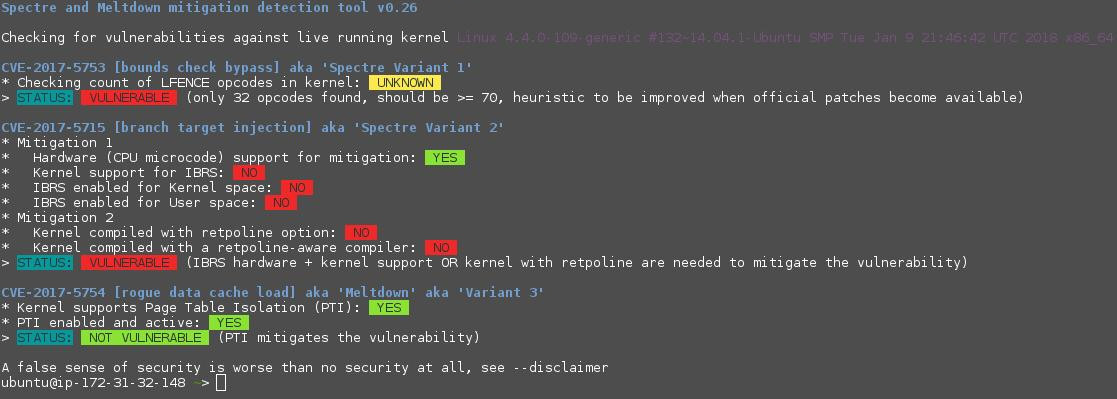
SSH to it and you can use this (script) which does a wonderful job at checking the kernel susceptibility to all known variants of Spectre/Meltdown:
wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
chmod a+x spectre-meltdown-checker.sh
sudo ./spectre-meltdown-checker.sh
You should see something similar to the screenshot below: